Monday, December 15, 2008
Unwiped devices and drives
Some people may never find out what they've released.
Implications of the Myspace Suicide case
When reading about this case, try to think if the punishment achieves one of the four goals and consider the aftermath and what it might mean for you in the future.
Doppleganger (again)
Sunday, December 14, 2008
Young people as a security threat?
Generation Y user behavior could endanger security of enteprise systems, studies say
Monday, December 8, 2008
Agent.btz visits the Pentagon
Friday, December 5, 2008
Your face is easy to fake
Perhaps we should move on to a more robust biometric system.
Wednesday, December 3, 2008
Linux vs Windows DOS commands
| Windows DOS | Linux/Cygwin |
|---|---|
| dir | ls |
| cd | pwd |
| cd [path] | (same) |
| cls | clear |
| copy [old] [new] | cp [new] [old] |
| del [file] | rm [file] |
| move [old] [new] | mv [old] [new] |
| tree | tree (Linux only) ls -R |
| mkdir [dir] | (same) |
| rmdir [dir] | (same) |
| help [cmd] | man [cmd] |
| type [file] | cat [file] |
| date /t | (same without /t) |
| time /t | date |
| netstat -an | (same Linux only) |
| netstat -rn | (same Linux only) |
| ipconfig /all | ifconfig -a (Linux only) |
For more information on Linux commands check out this tutorial or this tutorial (scroll past the ssh stuff).
Windows DOS Commands
| dir | list out files |
| cd | show current working directory |
| cd [path] | change to [path] directory |
| cls | clear screen |
copy [old] [new] | copies the old file to new |
| del [file] | deletes the file |
move [old] [new] | moves the old file to new |
| tree | shows the tree of the current directory |
| md | creates new directory |
| mkdir | creates new directory |
| rmdir [dir] | deletes directory dir |
| help | lists help information |
| type [file] | outputs file contents to screen |
| date /t | outputs date to screen |
| time /t | outputs time to screen |
| netstat | gives us network connection information |
netstat -an | -a: all connections -n: IP addresses |
netstat -rn | -r: routing information |
ipconfig /all | gives us network information |
Cygwin Installation
The setup file is here.
When you download setup, double click it. You should see the following:

Press ``Next'' and choose ``Install from the Internet'' :
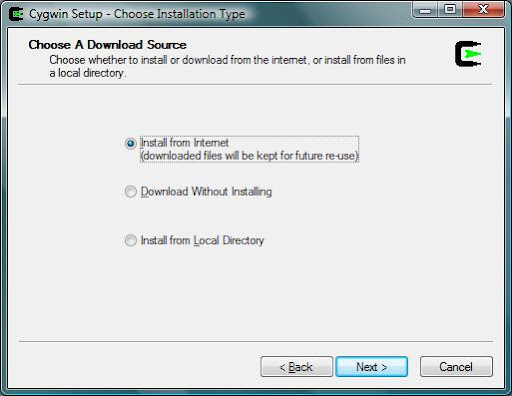
Choose where to install Cygwin (by default it is in C:\Cygwin):
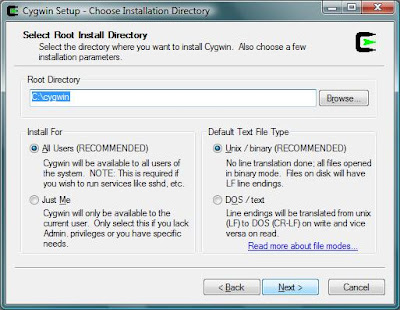 |
Cygwin will create a directory in which it will store the its files during installation. After installation you can delete the folder. The default location is the desktop:
 |
Select your internet connection. The default is OK:
 |
Select a mirror (mirrorservice.org is good):
 |
Press ``Next'' You should see the following:
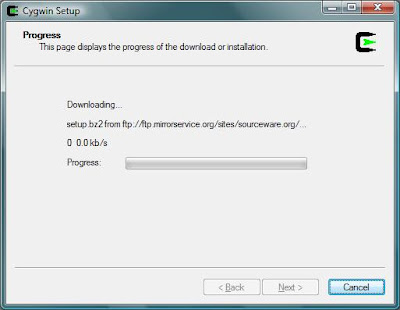
Next you will see a list of packages you can download. By default these are organized by category:
 |
If you press the plus signs on the left hand side, it will open up the category and you can select specific packages:
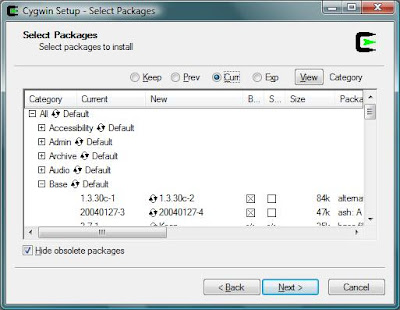 |
Here is a list of packages you need organized by category:
- From the Base category
- Everything
- From the Devel category
- Gcc: C, C++, Fortran compilers
- gcc-mingw: Mingw32 support headers and libraries for GCC
- gcc2: Version X.XX.X [whatever is latest] of C, C++, Fortran compilers
- gdb: The GNU Debugger
- make: The GNU version of the `make' utility
- mingw-runtime: MinGW Runtime
- openssl-devel: The OpenSSL development environment
- From the Editors category
- Nano: A pico clone text editor with extensions [works like pico]
- vim: Vi Improved – enhanced vi editor
- From the Interpreters category
- Perl
- Python
- From the Utils category
- until-linux: Random collection of Linux utilities
- file
- ELFIO
- From the Text category
- less: A file pager program, similar to more(1)
After you have made your selections, press next for installation to begin. This part is the actual installation, and may take some time. Just let it finish. After it finishes you will be asked if you want to create shortcuts on the desktop. Make sure to click Finish.
Running Cygwin
When you run Cygwin for the first time, it might take a little longer to start up. This is because it is configuring
a few more files for your environment. Then you should get a command line prompt that looks like:
You are now able to work on your programs at home on your windows machines.

Tuesday, December 2, 2008
Memory Images
Edit 12/3/08: Here are some more XP images
Full Screen
To make it easier for you to sort through the output of Volatility I've written a little perl script to create an html report of running processes, open files and dlls.
This is not finished as there is more information that I would like to correlate from the output of Volatility. But if you are somewhat curious, this is what I have so far: vol2html.pl. You can see an example report here. The output files for this report and the perl script are bundled together here. There is minimal error checking.
To use, first redirect the output of Volatility for pslist, dlllist and files to text files:
./volatility pslist -f mem.dd > pslist.txt
./volatility files -f mem.dd >files.txt
./volatility dlllist -f mem.dd >dlllist.txt
Then feed the perl script these files:
./vol2html.pl -pslist pslist.txt \
-files files.txt -dlllist dlllist.txt
Monday, December 1, 2008
Security Breaches
What To Do if Compromised - Visa (pdf)
The Breach Blog (information about recent incidents)
IR Preparedness
Changing the Face of IR
Let the Class Action Suit Begin
MIT Boston Transit Talk
Article about this talk's cancellation
Enjoy!
Sunday, November 30, 2008
XOR Demos
xordemo.c
xordemo2.cpp
A Sixty-Eight Year Old Code
Monday, November 24, 2008
Monday, November 17, 2008
Saturday, November 15, 2008
Tuesday, November 11, 2008
Renderlab
Friday, November 7, 2008
Does Google Know Too Much?
Google's gathering of information and making it available online is provoking outrage in Germany, triggered by such things as its Street View service to capture and post images of streets all over the world using car-mounted cameras. "These pictures, which are available for retrieval worldwide over the Internet, could easily be linked to satellite photos, address databanks, and other personal data," says Germany's federal commissioner for data protection Peter Schaar, who suggests that such information could be tapped for shady activities. The aggregate data Google has compiled makes many intelligence agencies seem "like child protection services" in comparison, says Hendrik Speck of the applied sciences university in Kaiserslautern. Peter Fleischer, whose job as Google's head of data protection is to defuse such concerns by shielding users' information, insists that nothing Google collects identifies any particular individual. Opponents such as author Gerald Reischl counter that Google cannot validate such assurances, and he warns that the free Google Analytics program that Web site owners use to keep tabs on usage patterns can be used for surveillance. Thilo Weichert, who heads Schleswig-Holstein's Independent State Agency for Data Protection, writes that most Google Analytics users do not realize that the service routes data to the United States. "This violates the data privacy laws protecting those who use the Web sites," he says. Weichert also complains of Google's non-transparent operation, and its refusal to disclose anything about its data management strategy except "what is absolutely necessary ... and then only under pressure."
Obama/McCain Hack
Why the Obama-McCain Hack may be bigger than you think
Oh Noes! Obama and McCain’s Campaigns Were PWND
US Government Detects Attacks on Obama and McCain Computers
Defaults and weaknesses
Here are a two recent examples:
A Security Lesson From the Joe the Plumber Snooper
Prisoner PWNS Correctional System - Security Admins Out to Lunch
Thursday, November 6, 2008
Doppelganger effect
Since anyone can sign up for Facebook, Myspace, Twitter, LinkedIn etc and can use fake information, what is preventing someone from creating a fake profile or Doppelgänger of the target? If the target person is really well known then the Doppelgänger will have no problem collecting lots of friends under false pretenses. The possibilities are endless for what the Doppelgänger could do in this position now.
The above scenario was tested when Shawn Moyer created a fake twitter profile for Gadi Evron, a security specialist. A fake profile on LinkedIn was also created for Marcus Ranum the CTO of Tenable Security. The potential for abuse is clear. From the article:
Moyer noted that on any given social network there are what he called, "linkwhores." These are people that will accept friend connections from anyone else. So the researchers sent out friend requests to people based on a Google search for people that had security in their profiles. Moyer claimed they had more than 50 connections within 24 hours. They also got invites from other people, among them was Ranum's sister who was also fooled by the bogus profile.
The security researcher did the same trick on Twitter for noted security researcher Gadi Evron. Moyer claimed that the bogus Twitter profile actually received an interview request from a journalist who was looking for a source to talk about the Kaminsky DNS flaw.
So perhaps some online presence is better than none. What do you think?
CBS Early Show
Daniel Sieberg explains how millions of people are socializing via internet and mobile sites without meeting each other, sometimes with life-altering consequences.
Watch CBS Videos Online
Disobeying Corporate Rules
Monday, November 3, 2008
Data loss in the age of information
Bugtraq
Partial Disclosure
The Web Hacking Incidents Database
Privacy Rights Clearing House
Data Loss Database (more information here)
How Can Government Improve Cyber-Security? (I)
How Government Can Improve Cyber-Security (II)
Laptop/Border Control
FISA and Border Searches of Laptops
Laptop searches at the border: No reason? No problem
When Will Social Networking Cripple Corporate Network Security
Videos
CNBC "Big Brother, Big Business"
Privacy is Dead Get Over It (I)
Privacy is Dead Get Over It (II)
Sunday, November 2, 2008
Capturing Keyboard Strokes
Sunday, October 26, 2008
Misc Terms
How Stuff Works
Wikipedia
Zonealarm
Comodo
Man-in-the-middle Attack
Wikipedia
ARP spoofing
DNS Poisoning
DNS Poisoning Video
Cookies
Wikipedia
Sidejacking
Gmail https
Gmail Activity
Tor
Wikipedia
Tor Website
Proxy
Wireless (Wifi)
Wired Equivalent Privacy (WEP)
Wi-Fi Protected Access
Airbase
Airsnort
Kismet
Ettercap
Top 100 Security Tools
Radio-frequency identification
Wikipedia
The Risk of ePassports and RFID
Elvis' RFID Passport
RFID reader
How To: Disable Your Passport's RFID Chip
How to Disable RFID tags
Monday, October 20, 2008
Wireshark lab: 10/22
rhino.log
rhino2.log
rhino3.log
Download each of these trace files to use with wireshark. For each of these network trace files do the following:
1) Look at the protocol column and write down each unique protocol that you see there.
2) Briefly describe 5 of the protocols from (1) - that is, what do they do/what are they used for? (We have covered a few protocols in class).
3) Use the search bar to see if you can find any image files. Image files often have file headers of JFIF, EXIF or GIF.
4) If you find any image files, write down the IP addresses that are involved in transmitting those files.
Saturday, October 11, 2008
Wireshark lab: 10/15
You will use the following trace files since you cannot do live capture in the lab.
After you have downloaded the above zip file, extract the contents onto the desktop.
You will do a lab on HTTP. The lab says ``Ethereal'' which is the old name for Wireshark, but the lab is still valid.
Start up Wireshark and open the file called http-ethereal-trace-1 that you extracted onto the desktop by choosing File->Open and then choosing the above file. You will use this file for all of part 1 in the HTTP lab. Each section uses a different trace file read carefully which trace file you need to use (each of the http-ethereal-trace files will be used).
Try to answer as many questions as you can. These will be figured into your grade as extra credit.
Monday, October 6, 2008
Network Tools
Chaosreader
Chaosreader can extract images from the network log files (though not all as we saw) and will print out a nice html report of all the flows.
Here is Chaosreader in action:
Full Screen
It can provide a nice start for making sense of the log file and locating connections of interest. However it doesn't extract all files of interest.
Etherape
Etherape allows you to see the traffic as a graphical representation. You can have it listen on a live device, or you can feed it a network dump file. Here is a video of etherape:
Full Screen
p0f
p0f is a passive OS identification tool. It uses three tests:
1) SYN packet test, where it watches outgoing SYN packets
2) Using the -A switch enables the SYN+ACK test
3) Using the -R switch enables the RST+ACK test
You can have it run on an interface by using the -i switch and interface name, or against a dump file using the -s flag.
snort
Snort is an intrusion detection system, but can also be used to read files. You have been supplied with alert files that were created by snort against the dump files given to you. When running snort you can use flags to make it read in a file. Here are the flags that were used to create the alert files:
# snort -c [config_file] -r [dump_file] -l [directory]
-c lets snort know which configuration to use
-r lets snort know which file to read
-l lets snort know where to write the log files
A brief snort video:
Full Screen
tcpdump
Tcpdump can be used to capture network traffic. When doing so, you let tcpdump know which device to use to read packets using the -i switch. If you want to save the traffic, you can use the -w switch. You can also specify the size of each packet saved by using the -s switch. Here is an example usage:
# tcpdump -i eth0 -s 1515 -w file.lpc
Tcpdump can also be used to read traffic data from a network dump file by using the -r switch followed by the name of the file you want to read. Here are some other switches you should use:
-n used to get only IP numbers
-nn don't translate IP and port numbers
-x used to get hex data of packets
-X used to get hex and ASCII data of packets
-c used to specify a number of packets
-e used to get link layer headers (MAC addresses)
One can also specify other items for tcpdump to look for in the traffic. Here is a TCP header:
With all TCP traffic there are flags that are associated with the conversation. Here are some flags of interest:
- SYN – Synchronize sequence numbers
- ACK – indicates an ACKnowledgment
- PSH – Push function
- RST – Reset the connection
- FIN - close connection
When a TCP connection is first made, there is a 3-way handshake that must occur before data can be sent. The handshake consists of:
1) A SYN packet sent to the server from the client
2) Response of SYN-ACK from the server
3) An ACK sent back to the server from the client
Seen below:
Therefore, one is often interested in SYN packets and can search for them using tcpdump. If you look at the TCP header you can see that the flags are located in the thirteenth byte. Therefore we can tell tcpdump to look in the thirteenth byte and give it the value. Since the SYN flag is the second one from the right, it has a value of 2 (think binary). So one usage is:
$ tcpdump -n -r [file.lpc] 'tcp[13]==2'
If you want to see packets with the SYN flag (and other flags) set you have to use bitwise AND:
$ tcpdump -n -r [file.lpc] 'tcp[13] & 2 == 2'
Likewise SYN+ACK has a value of 18, since the ACK flag is in location 4 (zero based) from the right which has a value of 16 and since SYN has a value of 2, we can change the total value to 18:
$ tcpdump -n -r [file.lpc] 'tcp[13]==18'
Or Hex:
$ tcpdump -n -r [file.lpc] 'tcp[13]==0x12'
You can also use the tcpflags option:
$ tcpdump -n -r [file.lpc] 'tcp[tcpflags]==2'
You can also indicate a particular host:
$ tcpdump -n -r [file.lpc] 'tcp[13]==2' and host [IP]
tcpxtract
Tcpxtract can be used to extract files from network dumps. We found that it crashed on some dumps with a segmentation fault however while we were doing our analysis.
tcpflow
Tcpflow is a really nice tool that can be used to rebuild conversations between two machines. Therefore we can use it to extract files. Here is a basic usage:
$ tcpflow -r [file.lpc] -c port [port number]
The -r switch works as before to indicate which file to read. The -c flag says put output to stdout. The port option lets one indicate which port number to use to construct a stream.
Here is a video of tcpflow being used to extract a JPEG file after finding it with chaosreader:
Full Screen
Therefore, if you have a lot of ftp connections, you can extract all files from the streams by using port 20 in the tcpflow command. Why port 20? Because an ftp connection uses two ports: 20 and 21. Port 21 is the control/command port (the connection all your typed commands go to) and port 20 is the data connection where the files get uploaded. You can use it on Venus, just issue the following commands:
$ wget
ftp://ftp.circlemud.org/pub/jelson/tcpflow/tcpflow-0.21.tar.gz
$ tar -xvzf tcpflow-0.21.tar.gz
$ cd tcpflow-0.21/
$ ./configure
$ make
The executable will be in the
tcpflow-0.21/srcfolder:
Wireshark et al.
You have been using wireshark for a while now. I will continue writing about it a bit later...
Full Screen
Friday, October 3, 2008
EC Homework
2) Collect about 3-5 minutes worth of traffic on your computer. Surf as you would normally on your computer.
3) Stop collecting and save the file as ``network_home.pcap''
4) Look at the protocol column and write down each unique protocol that you see there.
5) Briefly describe 5 of the protocols from (4) - that is, what do they do/what are they used for? (We have covered a few protocols in class).
6) What is your IP address?
7) If you click on the Protocol column you can sort the packets by protocol. You can also search for a particular protocol by typing it in the ``Filter'' area. Filter for the HTTP protocol. Right click on one of the green HTTP lines and choose ``Follow TCP Stream.'' What does the first line of the pink text say? What does it mean? What does the first line of the blue text say and what is it mean?
Extras
Wednesday, September 24, 2008
Monday, September 22, 2008
Networks
IP (internet protocol) address
NIC (network interface card)
MAC (Media Access Control) address
Port
DNS (Domain Name System)
Packet
netstat
ipconfig/ifconfig
ping
traceroute
We also learned about different internet protocols:
IP (Internet Protocol)
TCP (Transmission Control Protocol)
HTTP (HyperText Transfer Protocol)
HTTPS (The secure HyperText Transfer Protocol)
ICMP (Internet Control Message Protocol
UDP (User Datagram Protocol)
As well as a few others.
We also talked about a few applications that can be used to watch the network:
Etherape, shown below can allow you to see the traffic on your network. Unfortunately for most of you, it only installs under Linux and Mac OS/X:
Etherape Fullscreen
Wireshark is a packet analyzer that you can use to see the packets of information coming in and out of your computer. It easily installs under Windows and Linux. Here we are using it to get the password and username from a fake myspace account:
Wireshark Fullscreen
Here is a video of ping and traceroute commands:
Ping/Traceroute Fullscreen
Thursday, September 18, 2008
Talk on 9/24: Visual Forensic Analysis
The Center for Cybercrime Studies
The John Jay College of Criminal Justice
Presents
Visual Forensic Analysis
Speaker: Greg Conti
Computer Science Department
United States Military Academy
For decades hex was the common tongue of reverse engineers and forensic analysts, but we can do better. Hex editors are the Swiss Army knives of low level analysis and have evolved significantly, but are now at a local maximum. With the tiny textual window hex provides, it is difficult, if not impossible to understand the big picture context and inner workings of binary objects - files, file systems, process memory, and network traffic. While there are helpful tools to analyze the special case of executable files, little work exists to help address the general case of all types of binary objects. This talk presents visual approaches to improve the art and science of forensic analysis, diffing, and reverse engineering, both in the context independent case where little is known about the raw structure of the binary data and at the semantic level where external knowledge can be used to inform analysis. If you are faced with low level analysis tasks, you should attend this talk.
Greg Conti is an Assistant Professor of Computer Science at the United States Military Academy. His research includes security data visualization and web-based information disclosure. He is the author of Security Data Visualization (No Starch Press) and the forthcoming Googling Security (Addison-Wesley). His work can be found at www.gregconti.com and www.rumint.org.
Date: September 24, 2008
Time: 3:30 PM
Location: Mathematics Conference Room - 4238N
445 West 59th Street, New York City 10019
RSVP: Nicole Daniels at 212-237-8920 or email ndaniels@jjay.cuny.edu.
For additional information please contact Professor Doug Salane, Director of the Center for Cybercrime Studies, at 212-237-8836 or email dsalane@jjay.cuny.edu.
Secret messages
Good luck!
Palin's Yahoo account compromised
For someone who has such a high profile she should have at least thought of using some fake information for her user questions and better passwords.
More articles:
wikileaks
Wired
The upcoming aftermath:
Wired update
TheRegister
Let's see if this doesn't get blown out of proportion...
Sunday, September 14, 2008
Viruses (or virii) - Part 2
Popular subroutines used are:
- Document_Open() and
- Document_Close()
So we could write code in these subroutines that will execute when either the document is opened or closed.
We will create a word document and open the Visual Basic Editor:
Right click on the word document shown and click ``View Code'':
Choose ``Document'' on the right hand side and ``Open'' on the left:
We'll have a message box come out when the document is opened and we'll delete a file called ``test.txt''. Another message box will come out when the document is closed. The resulting code is shown below:
If macros are enabled on for MS Word, then the code will execute. An execution is shown below:
You should disable most macros to make sure that you are safe and to avoid viruses that use this method of transportation. You can do that by going to Tools->Options->Security->Macros and setting the setting to either High or Very High:
If you have your setting to Medium you will be prompted as to whether or not you want to execute macros:
Viruses (or virii) - Part 1
Viruses are not complete programs. They must reside in a host program in order to function and need human intervention in order to execute. Viruses can reside in any file, but are only affective if they are within a file that can be executed.
There are two types of executable files on Windows systems:
- COM
files that end in the COM extension which are relics of the old CP/M OS - EXE
files ending in EXE extension. Also includes PE (Portable Extendable) format (.SYS, .DLL, .OCX, .CPL, .SCR)
Companion Infection Technique
The virus may masquerade as a known program such as cmd or notepad and may use a different extension than the traditional program or may use a misspelled variation of the traditional program name. Since the virus needs to be executed in order to be affective, a program masquerading as a legitimate one could fool the user into executing it.
As we know we can run programs by going to Start->Run and typing the name of the program we want to run without the extension:
So if there is a program that contains the name written in the Run box above in the Windows path, it will execute. So we could see how easy it would be for a program with a name like notpad.exe (notice that the e is missing) to execute when the user mistakenly mistypes notepad in the Run box.
Another interesting thing about Windows is that .COM files are executed before .EXE files. It may be because the files come first alphabetically, or it may be due to the configuration of Windows. Either way, an attacker can use this to his/her advantage by creating an executable with a .COM extension and placing it in the same folder as the original executable. We will do that now.
In this example a program will be written in Visual Basic which you can get for free here. All it will do is flash a couple of message boxes and then run the real application. Here is the code:
After we compile the code and obtain the executable, we will set the property to ``hidden'' and rename the extension to .com:
The new program is then copied into the C:\Windows\System32 folder. Since it is a hidden file, it will not show up when you do a directory listing:
Now if we try to run notepad by using Start->Run we will get the following execution before notepad launches for real:
Now we see just how close we were to potential catastrophe. Most viruses will run without you knowing that they have executed and will run the program that was requested so that the user will not suspect anything. Viruses often multiply by writing themselves into other files that will be sent to other potential victims or executed later.
Other Virus Methods
A virus can also completely overwrite the host file, thereby replacing the original file with itself. Obviously this could alert the user, since previously working programs will no longer work.
A virus may also prepend (put itself at the beginning of the file) or append itself to a host file.
Viruses can also infect document files (Word Documents, Excel Documents etc) to activate when opening, closing or doing various other tasks. We will look at a document example later.
Computer basics
An Operating System (OS) is the a software program that works as the interface between the user and the hardware. Examples of Operating Systems are Windows XP/Vista, Linux, Mac OS/X, and Unix. Modern Operating Systems support multiple programs (processes) and multiple users at one time. The OS manages everything on the computer such as: programs that are running (processes), files that are open, network connections, users who are logged on (and their processes, files, etc), memory usage, etc.

A process is a program that is currently running (executing) on a computer. Every process running has a unique number associated with it called a Process Identifier (PID). This allows the Operating System to keep track of each process. A process that is running is currently in main memory or Random Access Memory (RAM).
Random Access Memory (RAM) or main memory is a volatile form of computer storage that for items that are currently being used on the computer. Processes (and data needed by the processes) that are currently running must be in RAM in order for them to run.
A Hard Disk or Hard Drive is a piece of hardware that is used for longterm storage. Every time you save documents and pictures they are on the hard drive.
A Central Processing Unit (CPU) is hardware that is the brain of the computer. All instructions by programs running on the computer are processed by the CPU.
A user is someone who is currently using the computer or programs on the computer.
A programmer is someone who creates computer programs. Programs are created using programming languages. Some example programming languages are C, C++, Java, Perl, and Python.
Binary is a numerical system that contains only 1's and 0's and is the basis representing ``On'' and ``Off'' switches in computer circuits. This is what the computer understands and speaks as a native language. Most computers use the ASCII encoding scheme to represent characters. You can find a table of these values here. Fun: ``There are 10 types of people: those who understand binary and those who don't.''
Hex (short for hexadecimal) is a base-16 numerical system that contains the characters 0-9 and A-F. Fun: ``How many people read hex if only you and dead people read hex?''
A Network Interface Card (NIC) is a piece of hardware that allows a computer to communicate on a computer network.
An Internet Protocol (IP) address is a numerical address for a computer on a network. An example of an IP address might be: 192.168.0.99
A Media Access Control (MAC) address is the hardware address of a computer on a network. It is assigned by the maker of the computer's NIC card. An example of a MAC address might be: 00:3G:2D:10:AF:7E
A Port is the result of a program on a computer that is connected to the network. This results in an ``opening'' on the computer to the network. There are 65536 ports numbered from 0 to 65535. Well known ports range from 0-1023, which means that we can usually tell which programs are running if we see these ports are open. This doesn't mean that these programs can't change ports, however, just that they normally run on these known ports. Here you can find a list of known port numbers.
Transmission Control Protocol (TCP) is a connection oriented network connection (like a phone call). For more information see Wikipedia.
User Datagram Protocol (UDP) is a connectionless network connection (like the mail). For more information see Wikipedia
Tuesday, September 9, 2008
Two network tools
# nmap -O 192.168.0.10
Starting Nmap 4.52 ( http://insecure.org ) at 2008-09-10 00:14 EDT
Interesting ports on 192.168.0.10:
Not shown: 1709 closed ports
PORT STATE SERVICE
135/tcp filtered msrpc
137/tcp filtered netbios-ns
138/tcp filtered netbios-dgm
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
MAC Address: 00:XX:XX:AA:99:44 (Intel)
Device type: general purpose
Running: Microsoft Windows 2003|XP
Too many fingerprints match this host to give specific OS details
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at http://insecure.org/nmap/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.992 seconds
Wireshark is a packet analyzer that you can use to see the packets of information coming in and out of your computer. It easily installs under Windows and Linux. Here we are using it to get the password and username from a fake myspace account:
Wireshark Fullscreen
Software Issues
Here is a small example of a buffer overflow, but more often something like this example will not occur. The error will be exploited to do something more malicious, like to execute other commands on the machine.
Direct link
Examples: virtual mugging
Slammer Worm
Command Injection: occurs when input is passed directly to an interpreter. Here's a video example:
Direct link
Cross-site Scripting (XSS): occurs when an application running on a web server gathers data from a user in order to steal it.
Failure to handle errors: occurs when a program encounters a problem that it is not prepared to handle. It is up to the programmer to make the program handle all anticipated errors. The programmer should make sure that should the program encounter an error, that it report what the error was before it ends execution.
Failure to protect network traffic Since sensitive information (usernames, passwords, emails, chats) often crosses the network, care should be taken to protect it.
Wireshark Fullscreen
Failure to Store/Protect Data: programmers should keep secret information out of programs (passwords, keys, other sensitive information). Hard coded information can be extracted out of the executable if someone knows how to do this:
Direct Link
Failure to use cryptographically strong random numbers. If the numbers used to encrypt data are easy to guess, then cryptography is useless to hide the information.
Example: Debian OpenSSL
Format string problems occurs whenever the input to certain print functions is not sanitized before it is passed to the function. This could allow an attacker to figure out things about the program and where parts of it lie in memory.
Direct link
Neglecting change control. Developers must be sure that the working system given to a customer represents their intent and that all future updates are well tested and approved.
Improper file access. Users should not have access to sensitive files unless they are the administrators of the machine in question.
Improper use of SSL. If SSL is misconfigured it could allow access to data in an unencrypted state and dangerously give a false sense of security.
Information Leakage besides the direct human factor (``loose lips sink ships'') from a software point of view information could be inadvertently leaked as well. An example of this could be timing attacks. For example, suppose it takes a password authentication program x seconds if the user successfully enters his/her username and password, y seconds if the password is incorrect but the username is correct and z seconds if the username and password are both incorrect. From this, an attacker can indirectly verify the validity of a username and launch a more educated attack on the password system.
Integer bugs exists when an integer used as a variable to indicate the amount of memory is to be allocated is not checked before memory allocation.
Race conditions. Sometimes programs do not execute at the exact time that we think they should. Sometimes processes can stall or slow down while running. An attacker could take advantage of this by switching a file before it is accessed.
SQL Injection occurs when the attacker places commands into the input form that are then executed. It may be used to gain access to sensitive data, to delete data or for other means.
Trusting Network Address Resolution. Unfortunately as we learned earlier, it is not always a good idea to trust protocols like ARP and DNS. We learned that there exist flaws in these protocols that could allow an attacker to insert himself/herself in the middle of the conversation. Here is a video of DNS spoofing.
Unauthenticated Key Exchange. If you do not authenticate the entity with which you are obtaining the key, there is no way to verify its identity.
Use of magic URLs and hidden forms. Unfortunately sometimes a URL contains sensitive information that should not be there. This can be observed by an attacker as the http request goes by. Even though a hidden form might be used by a webprogrammer, an attacker can simply view the source of the webpage in order to gain the sensitive information.
Use of weak password-based systems. If the password is easy to guess, what's the point?
Direct link
Finished product (3 min later)
Google Chrome
Public Announcement
Story Behind It
Google Chrome release was irresponsible by Sippy
Why I'm not running Chrome anymore (back to IE8 beta 2 for me) by Robert Hensing
LookingGlass Vendor of the week: Google by David Maynor
milw0rm
BugTraq
CSAW Competition
+ Security Quiz
+ Application Security CTF
+ Forensics Challenge
+ Essay Contest
+ Awareness Poster Design Competition
+ Embedded System Challenge
+ Research Poster Competition
You may compete alone or in a team if you like. You must register in order to compete. Registration ends Sept 11th so sign up quickly! It costs nothing to participate and there are cash prizes for winners. Check out the details for each of the competitions online.
Death Star Threat Modeling
Part 1
Part 2
Part 3
Integrity matters
1. Boredom
2. Intellectual challenge
3. Revenge (disgruntled employee)
4. Sexual gratification (stalking, harassment)
5. Economic
6. Political (terrorists, spies)
7. Fame
We also discussed cases in which the perpetrator was hired as a security consultant after the incident (and often by the very company s/he penetrated). The question arises: ``Should people be given a second chance?''
On one hand, you have the argument that this person is highly skilled, so who better to have as a security consultant? S/he already knows the security issues of the company in question. S/he knows what things to protect against. Also don't people deserve a second chance? People can change and not everyone is a recidivist.
On the other hand, how can you trust someone who just penetrated your network and therefore knowingly broke the law? There is already an issue with the moral fiber of the perpetrator due to his/her actions in the incident. How can we know that this person will not do something illegal in the future either against this company or someone else in the future? There are other issues that cause one to question hiring this person - not just because s/he has questionable tendencies, but also because there may have been little actual skill involved in the penetration itself. The person could have gotten lucky, or just used a common tool and may not really understand the technical matters of the attack itself. Also it is often argued that it is much easier to break something than to protect it from potential threats. Therefore just because someone breaks into a network does not mean that they are an expert (there are numerous exceptions to this however).
There was an interesting blog post by Richard Beijtlich of Tao Security about this subject of trusting ``reformed hackers'' (remember I don't like using the term hacker in a negative light like this, but this is from the article...). I don't know enough about this particular case mentioned to cast any opinions and certainly don't want to draw any malicious attention my way, so I'll let you read the article and come to your own conclusions. Make sure to read the comments as well.
Perhaps it would be better to hire this person after sufficient time has passed since the incident (after s/he has proven himself/herself trustworthy). However, doubts will most likely remain.
What are your thoughts about this?
[1] Marjie Britz, Computer Forensics and Cyber Crime: An Introduction
Prentice Hall, 2004
Friday, September 5, 2008
Hackers
We even talked about how things can get exaggerated in the eyes of the media, by watching a Fox Special on ``Hackers on Steroids'' which demonstrates the media's hype of ``hackers'':
One of the items mentioned here, however was how a boy's myspace account was ``compromised'' several times. Myspace actually sends usernames and passwords in the clear, so it could be obtained. However, most of the time usernames and passwords are obtained by Phishing, where the user is tricked into giving their information. [We will talk more about phishing later...]
There is actually more to the story on the fellow in the Fox Special, however. You can search around for the details on your own ...
Myspace Passwords
Bruce Schneier's blog
Brian Kreb's blog
They also talk about a few exploits that were used to obtain the account names and passwords.
There was a recent case about a stalker who harassed Amor Hilton on Myspace.
Also, don't think that you are safe just because you have a ``Private Profile.'' Weaknesses in the Myspace website allowed access to people's private pictures and information. Myspace had known about the flaw for sometime, but still hadn't fixed it.
Tuesday, September 2, 2008
Three Approaches to Security
Here is a list of the three things:
1) Security by Correctness
2) Security by Isolation
3) Security by Obscurity
I want you to read this post, because it is very interesting... We will discuss it next week as well. I don't want you to forget it, because it may very well end up on a quiz someday... :-)
9/3/08: Notes and Personal Security
Extras:
Social Engineering
We will discuss Social Engineering in the class and also talk a little about one of the best known social engineers. Here is a video on how to social engineer a free pizza:
The Social Engineering Panel at The Last HOPE
C|Net article on this panel
Pretending to be something you aren't
We will discuss an article from wired about a mole from the media who attended Defcon. The organizers suspected that she was in fact a reporter, in spite of the fact that she refused to buy the media pass instead of the regular one. She was hoping to out agents and others doing ``illegal activities'' and even commented on
How the people in Kansas would be interested in what takes place [at such events].
She then made the mistake of telling others her intent and revealing her hidden camera, so her unveiling was inevitable:
Phishing
We will also discuss Phishing, which is a type of social engineering. Here is a Phishing IQ test so you can see how tricky some of these guys can be.
We will take a look at a fraudulent email I received and a whois lookup to see which country the email is coming from. This is a Nigerian Letter or 419 fraud letter. There is a website called 419eater that is dedicated to fighting these fraudsters.
Bullying
Megan Meier was a teenager with some teenage problems who was duped by some ``friends'' including the mother of one of these friends. They had created a fake profile of a teenage boy and engaged in conversation with Megan. Eventually, they started to harass Megan with the fake profile and she took it rather badly and killed herself.
Here are some articles:
http://www.news.com/8301-13860_3-9819394-56.html
http://blog.wired.com/27bstroke6/2007/11/blog-readers-ou.html
http://blog.wired.com/27bstroke6/2007/11/megan-meier-sui.html
Some readers became so outraged that they outed the adults that had duped Megan and posted not only their names, but places of business, phone number and address. Then one of the bloggers who had outed them got outed herself:
http://www.wired.com/politics/onlinerights/news/2007/11/vigilante_justice
An even odder turn in the case, is that of a blog that surfaced as a comment in another article called ``Megan Had it Coming.'' The writer of the blog at some point ``confessed'' to being Lori Drew, or the mother of the child who was friends with Megan, and had harassed her to her death.
http://www.dvorak.org/blog/?p=14913
http://sigmundcarlandalfred.wordpress.com/2007/11/19/megan-the-bitchhad-it-coming-or-how-to-kill-a-child-twice/
http://www.cnn.com/2007/US/12/08/internet.suicide.ap/index.html
The blog was posted here:
http://meganhaditcoming.blogspot.com/
It was recently revealed that the blog was a creation of an Internet Troll.
Thursday, August 28, 2008
Anatomy of a malware scam
Tuesday, August 26, 2008
Welcome to Math 270
This blog will contain extra class notes should there be any. More information will be available later.
Don't forget to sign up for the listserve:
Subscribe to math270 |
Visit this group |